LoRaWAN overview

LoRa (short for Long Range) is a modulation technique that is used in LoRaWAN networks for low-power, long-range wireless communications on the sub-1GHz band.
LoRaWAN is a media access control (MAC) protocol for wide area networks (WANs) that uses low-power, long-range wireless communications to connect Internet of Things (IoT) devices. It is based on the LoRa modulation technique, which allows for long-range communications at low data rates, and is designed for use in unlicensed sub-1GHz frequency bands. LoRaWAN networks are typically composed of gateways, which are connected to the internet, and end devices, which are the IoT devices that communicate with the gateway.
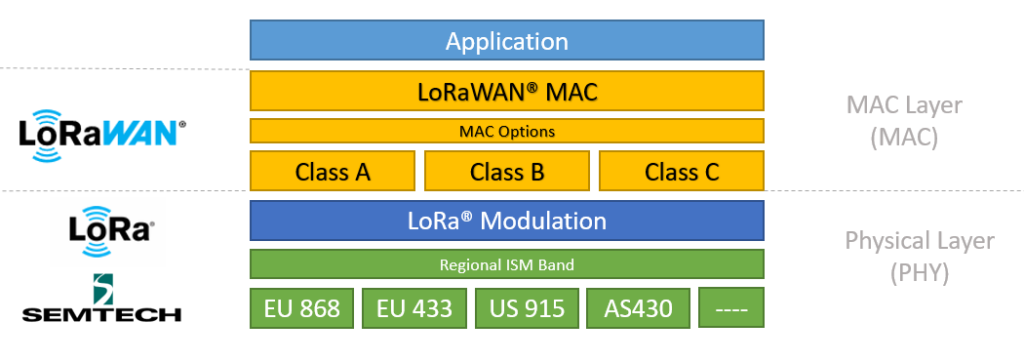
The protocol uses a star topology and supports both mobile and static devices. LoRaWAN provides mechanisms for secure communication, including secure over-the-air activation and end-to-end encryption.The protocol enables the deployment of large-scale and low-cost IoT networks. It’s an open standard and is both maintained and standardized by the LoRa Alliance, a non-profit association of companies, organizations, and individuals.
The Media Access Control (MAC) layer in LoRaWAN is responsible for managing access to the shared radio spectrum and coordinating communication between devices in the network. It provides mechanisms for device activation, secure communication, and message transmission and reception.
One key feature of the LoRaWAN MAC is its use of a time-division multiple access (TDMA) scheme, which divides the available radio spectrum into time slots that are allocated to different devices. This allows for efficient use of the limited spectrum and reduces the likelihood of collisions between transmissions.
Spreading Factor
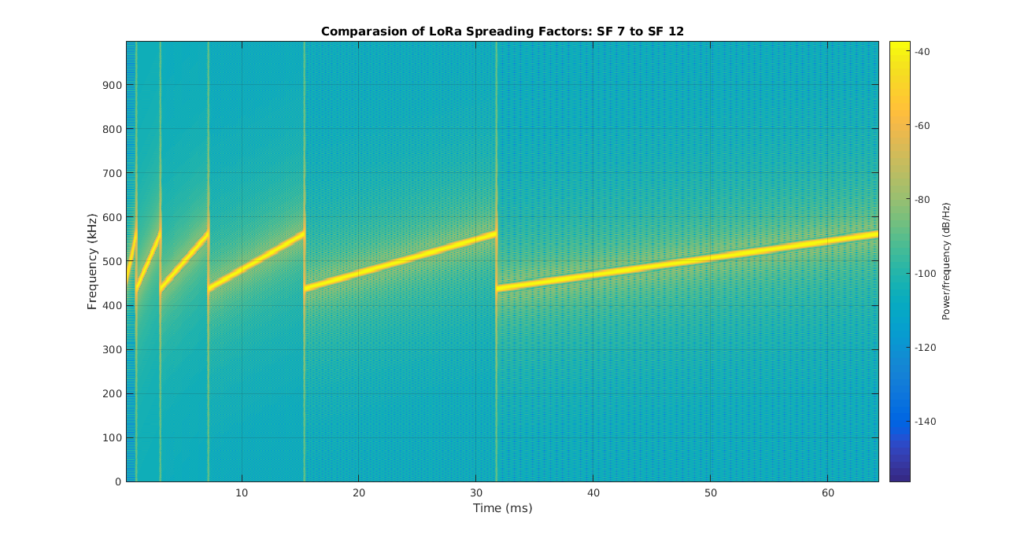
In LoRaWAN, the spreading factor (SF) is a parameter that controls the trade-off between data rate and range in the communication. It is used to spread the data over a wide frequency band, which increases the signal-to-noise ratio (SNR) and the robustness of the communication to noise and interference.
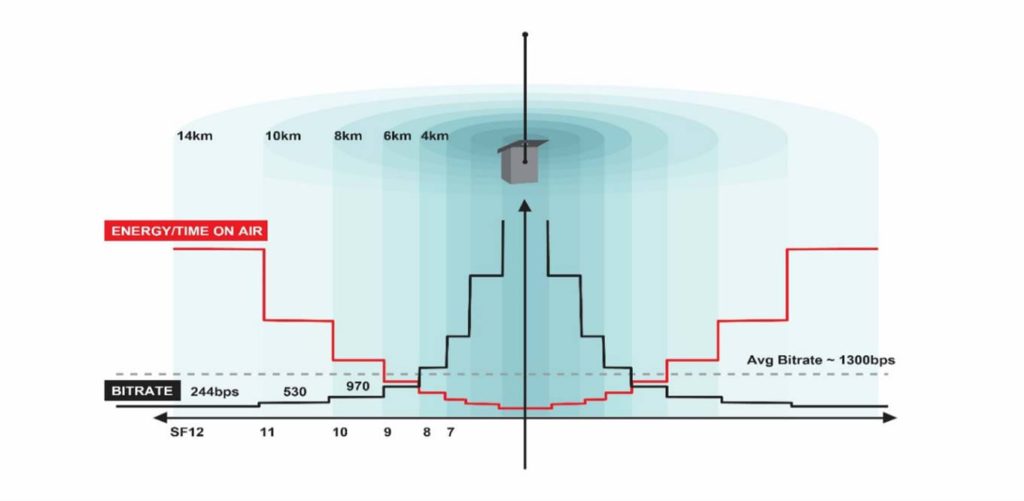
The spreading factor is inversely proportional to the data rate, meaning that as the spreading factor increases, the data rate decreases and vice versa. The spreading factor is a number between 7 and 12, with a lower number indicating a higher data rate with shorter range, and a higher number indicating a lower data rate with longer range.
When the SF is lower, the signal is spread over a wider bandwidth and the receiver can detect it with a higher signal-to-noise ratio, allowing for a higher data rate.
When the SF is higher, the signal is spread over a narrower bandwidth, which reduces the data rate but increases the range of the communication.
In a LoRaWAN network, all devices use the same frequency ban; the spreading factor is used to separate the devices and make them work in the same frequency band without interfering with each other.
The spreading factor can be adapted dynamically by the Adaptive Data Rate (ADR) algorithm, this allows devices to adjust their data rate and transmission power based on the radio conditions and the requirements of the application — this helps to optimize the trade-off between range and throughput.
LoRa Modulation
LoRa uses a type of spread-spectrum modulation, which means that the data is spread over a wide frequency band, allowing for a larger signal-to-noise ratio (SNR) and better immunity to interference. LoRa uses a chirp spread spectrum (CSS) modulation, where the signal frequency changes (or “chirps”) over time. This allows for a wider signal bandwidth and a higher data rate than traditional frequency-shift keying (FSK) modulation.
The LoRa modulation technique uses a low data rate, typically 0.3 kbps to 50 kbps, which helps to reduce power consumption and increase the range of the communication. LoRa signal can travel over long distance with low power; it can reach up to 15km in open field and 2-5km in urban area.
Additionally, LoRa uses a technique called Adaptive Data Rate (ADR), which allows devices to adjust their data rate and transmission power based on the radio conditions and the requirements of the application; this allows to optimize the trade-off between range and throughput.
The LoRa modulation technique is well-suited for IoT applications that require long-range, low-power communication, such as smart metering, asset tracking, and sensor networks.
Device Classes
The MAC layer also includes the LoRaWAN Class A, B and C, that defines the behaviour of the devices in terms of the communication between them and the gateway, enabling devices to be battery-powered and have low duty-cycle.
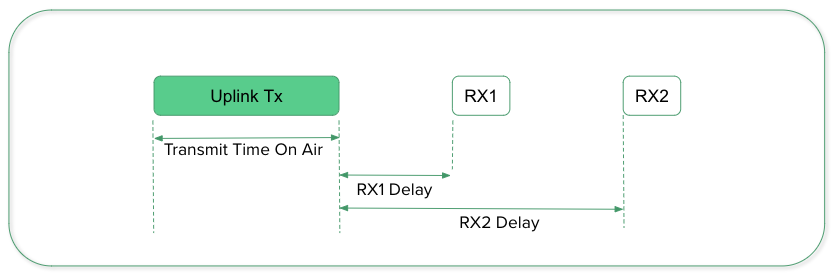
Class A devices are the most power-efficient and are intended for battery-powered applications. They have a low duty cycle, which means they spend most of the time in a low-power sleep mode and only wake up briefly to listen for incoming messages or to send their own. They have two receive windows, one after the end of the transmission and another 8 seconds later; this allows the device to conserve energy while still being able to receive downlink messages.
Class B devices have a slightly higher duty cycle than Class A devices, as they wake up periodically to listen for incoming messages even when they are not transmitting. This allows for improved bidirectional communication and enables applications such as over-the-air firmware updates.
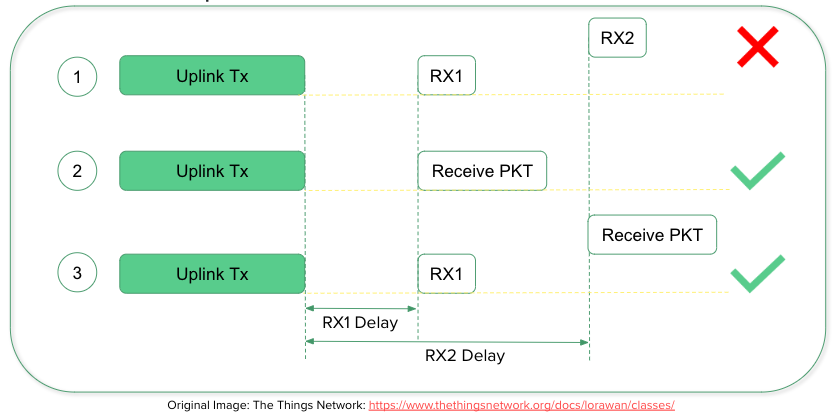
Class C devices have the highest duty cycle, as they are always listening for incoming messages when they are not transmitting. This allows for the fastest possible communication, but also results in the highest power consumption. This class is used for devices that need to be always reachable and responsive.

By choosing the appropriate class for a device, it is possible to balance the trade-off between power consumption and communication performance for a given application.
Device Activation
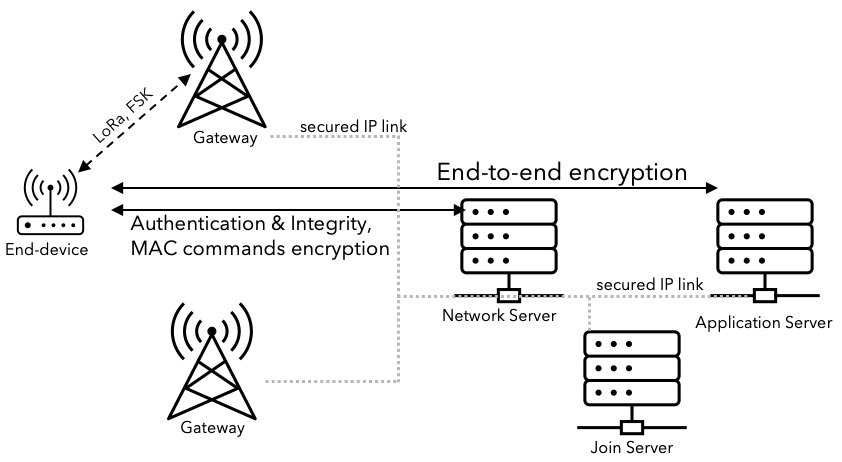
Over-the-air activation (OTAA) is a mechanism in LoRaWAN that allows devices to securely join a network and obtain the necessary credentials to communicate with the network. End-to-end encryption is used, which helps to protect against unauthorized access and tampering with the data. OTAA is the preferred method compared against ABP (Authentication by Personalization), which should only be used for quick testing in a lab environment.
When a new device is powered on and wants to join the network, it uses the OTAA process to request access. The device generates a unique device identity (DevEUI) and a device specific encryption key (AppKey) and sends them in a join request message to the network server. The network server then verifies the device’s identity and, if it is authorized, generates a unique network session key (AppSKey) and a network address (DevAddr) for the device.
The network server then sends the AppSKey and DevAddr back to the device, encrypted using the device’s AppKey. The device can then use the AppSKey and DevAddr to securely communicate with the network and send and receive data.
Adding Devices
In LoRaWAN, the join key is a unique encryption key that is used to secure the over-the-air activation (OTAA) process. The join key is shared between the device and the network server and is used to encrypt and decrypt the join request and join accept messages.
The device generates a unique device identity (DevEUI) and a device-specific encryption key (AppKey) and sends them in a join request message to the network server. The network server then verifies the device’s identity and, if it is authorized, generates a unique network session key (AppSKey) and a network address (DevAddr) for the device. The network server then sends the AppSKey and DevAddr back to the device, encrypted using the device’s AppKey.
The join key is used to ensure that only authorized devices can join the network and that communication between the device and the network is protected by encryption. The join key is typically pre-provisioned on the device before it is shipped, but it can also be provisioned after the device is deployed using over-the-air provisioning (OTAP).
It is important to keep the join key secure and to provision the devices with unique keys, otherwise an attacker could potentially use a compromised key to join the network and access sensitive information.
Sláinte!
Resources
LoRaWAN Alliance
TS001-1.0.4 LoRaWAN L2 1.0.4 Specification
LoRaWAN Security Whitepaper
https://lora-alliance.org/wp-content/uploads/2020/11/lorawan_security_whitepaper.pdf
LoRaWAN RP002-1.0.4 Regional Parameters
https://resources.lora-alliance.org/technical-specifications/rp002-1-0-4-regional-parameters