Wi-Fi Security Trends from Aruba Central
HPE Aruba Networks provided an excellent overview of WI-Fi 7 and WPA3 observations during their AP730 and Wi-Fi 7 update as part of the Network Field Day Exclusive at HPE Discover from Tech Field Day (TFDx) during the HPE Discover Aruba Atmosphere event.
The observations were based on many data points from customer devices connected to the Aruba Central management system. I do recommend watching the video to hear more about other topics discussed, including topics like:
- AP730 campus access point
- 320 MHz wide channels
- Improved indoor GPS accuracy
- Wi-Fi 7 PHY rates – in reality
- Preamble puncturing
- Beacon Protection
- WPA3-SAE with AKM:24
Out of all the content covered during this presentation, I want to focus on one specific slide, presented by Josh Schmelzle, which summarized the security protocols deployed across WLANs based on data sourced from Aruba Central customers.
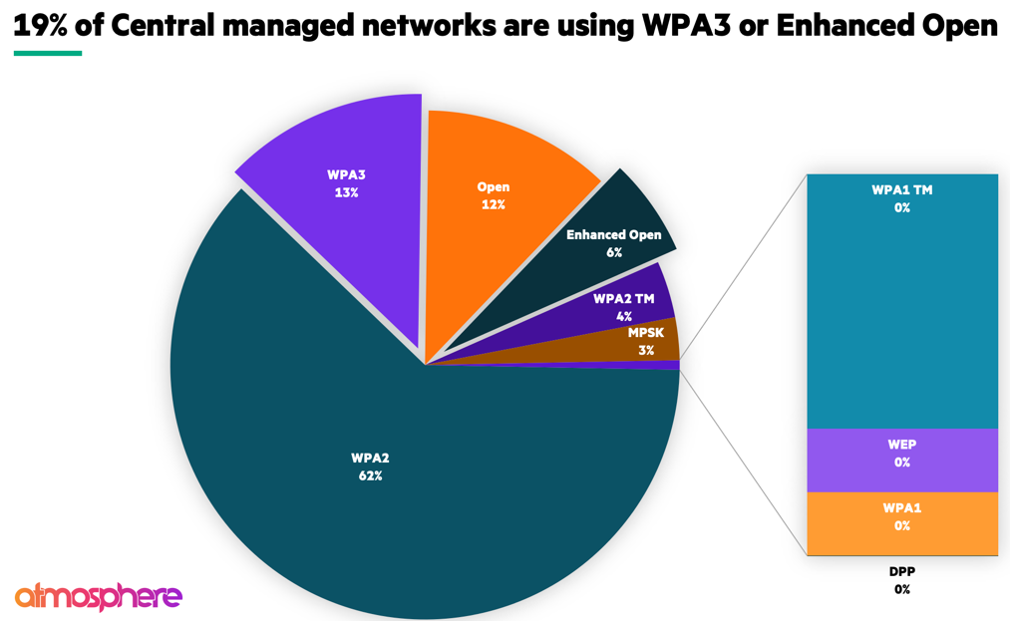
There is a lot to unpack here, so let’s start with the easy stuff. Protocols like WEP and WPA have long been deprecated, and most enterprise WLAN interfaces no longer provide easy access to configure WEP or WPA. Let’s be real: WEP and WPA are about as welcome in a modern WLAN as a floppy disk at a data centre. They are from the Jurassic period of wireless networking, and like dinosaurs, they should have gone extinct. They might still exist in some dusty corners of the network universe, but let’s face it: most enterprise WLANs have long moved on. Thankfully, Aruba’s data confirms this suspicion – adoption is sitting comfortably at 0% for WEP, WPA, and WPA Transition Mode (TM).
It’s worth mentioning that WEP and WPA may still appear in customer environments. It’s also a best practice to regularly perform security audits to detect poorly configured SSIDs using WEP or WPA. Such anomalies may occur when employees unmaliciously connect rogue APs to the corporate LAN to shortcut a business procedure while attempting to complete tasks easier or faster. This could also occur during major sporting events when access to live-streaming content is filtered over the corporate WLAN but not via the wired network. Furthermore, employees have even connected to neighbouring guest WLANs to circumvent live-streaming content filters during World Cup, Tour France, or any other significant sportsball event.
Now, before we pat ourselves on the back too hard, let’s address the elephant in the room: WPA3: adoption. Despite being the gold standard for Wi-Fi security and widely supported on Aruba Central APs, it’s only been embraced by a mere 13% of devices.
Why the hesitation? Well, some folks might be clinging to the “if it ain’t broken, don’t fix it” mentality. Others might be harbouring unfounded fears about compatibility issues. And then there are those who simply haven’t gotten around to it yet (hey, we’ve all been there).
Today’s gold standard for Wi-Fi security is WPA3, which has long been supported across all Aruba access points in Central via simple firmware updates. I must admit it was disappointing to see that WPA3 adoption was only at 13%. Perhaps WLAN administrators are unaware of how pervasive WPA3 has become across client devices. Perhaps they’re reluctant to enable it, worried that it might introduce some obscure, unknown incompatibility that prevents client devices from connecting. I’m sure everyone reading has the expression, “If it’s not broken, don’t fix it,” echoing through their thoughts.
If you’re interested in a deeper discussion about WPA3 deployment strategies, particularly when combined with enabling 6 GHz, I encourage you to read “Wireless Security Architecture” by Jennifer Minella. Additionally, the Wi-Fi Alliance has recently published a deployment and implementation guide documenting best practices for deploying WPA3 and OWE from their perspective.
Each WLAN admin needs to decide how to configure WPA3 to mitigate security risk while also avoiding any disruption to client connectivity, which is unique. There are some guidelines, but as they say, the devil is in the details. In fact, it is often better that this decision be part of a consensus agreed upon by multiple stakeholders. So read the documents linked above, and then start engaging with stakeholders to move forward to empower your WLAN with WPA3.
Let’s be honest – WPA2 has overstayed its welcome. Sure, it’s the trusty old workhorse of Wi-Fi security, the one we’ve all come to rely on (a whopping 62% of WLANs agree, according to Aruba Central). But let’s not kid ourselves – it’s been around since the Ice Age period of wireless networking, and, like a woolly mammoth, it’s starting to show its age.
Now, don’t get me wrong, WPA2 isn’t completely useless. It’s still compatible with most devices, and let’s face it, few of us relish the thought of incompatibility issues. Ultimately, WPA2 is vulnerable to offline brute force dictionary attacks. In other words, if someone really wants to get their hands on your precious data, they can capture it now and crack it later. It’s not exactly comforting.
Takeaway: Dance like no one is watching, encrypt like everyone is.
Circling back to WPA3, it’s not just a minor upgrade; it’s a complete overhaul of Wi-Fi security. Most importantly, it’s immune to those pesky offline brute force attacks that plague WPA2. That alone should be enough to make any security-conscious WLAN admin drool.
WPA2 TM has a small deployment, with 4%. Transition mode is a neat idea to bridge the gap in time until all WPA2 clients can support WPA3, but let’s be honest; it’s really just a band-aid solution. As only a firmware upgrade is required to transition from WPA2 to WPA3, it’s a more palatable solution than the transition from WEP to WPA2. In the dark ages of Wi-Fi, changing from TKIP (WEP) to AES (WPA2) required a hardware forklift to process the increased computational load. The Wi-Fi Alliance devised WPA to buy the industry time and reduce risk until chipsets were physically replaced with new hardware that could support AES.
WPA2 is ultimately vulnerable to offline brute force dictionary attacks, and capturing encrypted traffic today, especially if it’s high-value data, is worthwhile, knowing it may be crackable in weeks, months, or years. WPA3 is NOT vulnerable to offline brute force dictionary attacks, which is a significant advantage over WPA2 and a primary reason to upgrade.
So do yourself a favour and start planning your full WPA3 migration now. Read the documentation, engage your stakeholders, and make it happen. Your WLAN (and your data) will thank you!

Let’s dive into the remaining slices of the Wi-Fi security pie chart. We’ve got open networks (hello, coffee shop Wi-Fi!), OWE (the new kid trying to make open networks less sketchy), and the often-overlooked MPSK (the unsung hero of PSK management).
Open networks are ubiquitous in public spaces. They’re convenient, sure, but let’s be real, they’re also a security nightmare. Who hasn’t connected to a “Free Airport Wi-Fi” network and instantly regretted it?
Pro tip: if you’re doing anything even remotely sensitive (like online banking), use a VPN, or better yet, stick to cellular data (also with a VPN).
Opportunistic Wireless Encryption (OWE) is the Wi-Fi Alliance’s attempt to make open networks less…well, open. It’s a clever bit of tech that allows devices to negotiate encryption keys on the fly, without needing to distribute passphrases post-hoc. This means coffee shop baristas and hotel staff are no longer burdened with handing out authentication information to guests. Guests still benefit from encrypted traffic sent across the air gap between their Wi-Fi devices and the access point. It’s a step in the right direction but not a silver bullet. Remember, OWE only encrypts traffic between your device and the access point, it does not provide authentication. Once it leaves the AP, it’s fair game. Radios with 6 GHz capabilities have mandatory support for WPA3, OWE, and MFP (management frame protection). Migrating to a 6 GHz-only WLAN has a significant security boost that comes along for free.
MPSK (Multiple Pre-Shared Key) is an often overlooked technology. Most enterprise vendors support this functionality, although because it’s not an official standard, each refers to it by a different name. Some vendors include this functionality within a single solution, while others require additional NAC appliances like ClearPass to provide this function.
So, what is MPSK? Well, it allows WLAN admins to create individual PSKs or groups of PSKs that individuals or groups of devices can use to connect the same SSID. Traditionally, all devices are configured with the same global PSK. Rotating or purging the key becomes challenging because a new key must be distributed to all users simultaneously, or connectivity will be interrupted after a PSK rotation or change.
Over the course of business, employees may leave the company, devices may get lost, and 90-day password rotation policies may kick in, which will drive the need to change keys to revoke access. With unique individual keys, only the PSK for that individual employee needs deletion, while all other unique keys continue to function without interruption. Different groups of devices could have different PSK complexity requirements and all the keys could be linked to self-expiring time frames.
Users granted access to the internet for 24 hours may only need short, lower-case, alphanumeric phrases. Longer-term users may require longer, more complicated passphrases that also include punctuation or a mix of upper and lower case. A guiding principle here should be making things easy enough for users to choose to use the Wi-Fi network without being encouraged to find workarounds to authenticate themselves or their devices.
Some of you may wonder why not just use 802.1X and be done with it. Well, sometimes, it is just not that simple. Many IoT devices do not support 802.1X and sometimes layer 8 gets involved. I once worked with a customer who felt that if they pushed out a profile or certificate to any client device and that device stopped working or behaved differently, for whatever reason, the customer would be blamed and then required to fix the end-user device. Handing out a simple passphrase allowed them to wash their hands of responsibility for any change of behaviour on the client device and the responsibility to restore. End users did not see adding passphrases as invasive as installing a profile. Bizarre, I know, but when do Wi-Fi end users sound normal?
Lastly, I will point out one disadvantage of WPA3 – it breaks MPSK, rendering it no longer possible to distribute individual or unique group keys to devices or users. This was a very effective way to segment devices and manage lifecycles. Some vendors have devised a patent-pending way to address this with WPA3, but it is a crude hack. With only 3% of Aruba Central users leveraging MPSK, it is not a significant challenge that needs to be overcome. Still, a few entrenched organizations will have to pivot their security posture and may be noisy about it.
For comparison purposes, the graph below from WiGLE.net shows Wi-Fi security trends across scanned networks. WiGLE launched in 2001 with the goal of educating users and placing pressure on manufacturers to improve WLAN security. Most people back then, and even perhaps today, did not realize their private WLANs could be accessed by anyone over large distances using high-gain antennas and amplifiers. The data collected by WiGLE includes enterprise—and residential-grade WLANs and is vendor-neutral. There are regular competitions to measure who can detect the most networks possible.
The data from WiGLE aligns with the data from Aruba Central. Unfortunately, neither of the graphs I’ve included breaks down WPA2 usage into PSK vs 802.1X-based authentication, as it would be interesting to see how many PSK-based networks could potentially benefit from MPSK-style deployments.
Sidenote: It is possible to locate another person’s residence. As all detected SSIDs are captured with GPS location, location can be recovered via captured probe requests and matching the SSID names. Additionally, a list of nearby SSIDs from a Wi-Fi scanning application could reveal a unique location based on nearby SSIDs.

Slàinte!
Resources
WiGLE.net
Wi-Fi Alliance
https://www.wi-fi.org/wi-fi-download/47054
Time to Crack Passwords from Hive Systems
Wireless Security Architecture by Jennifer Minella
Wi-Fi in the Real World with HPE Aruba Networking (TFDx)