A Guide to Decrypting WPA2-Enterprise in Wireshark
Occasionally troubleshooting Wi-Fi connectivity requires analyzing the headers of Wi-Fi frames. Other times, digging further up the OSI stack at layer 3 and 4 is necessary. This latter case is complicated by the fact that most Wi-Fi traffic is encrypted at layer two using WPA2. Fortunately, with a few pieces of information, we can decrypt WPA2 traffic directly in Wireshark using a built-in decoder.
To decrypt WPA2-PSK traffic a few pieces of information are required. The Passphrase or PSK must be known and all 4 frames from the 4-way handshake must be present in the PCAP. Without these four frames, Wireshark will not be able to decrypt the traffic.
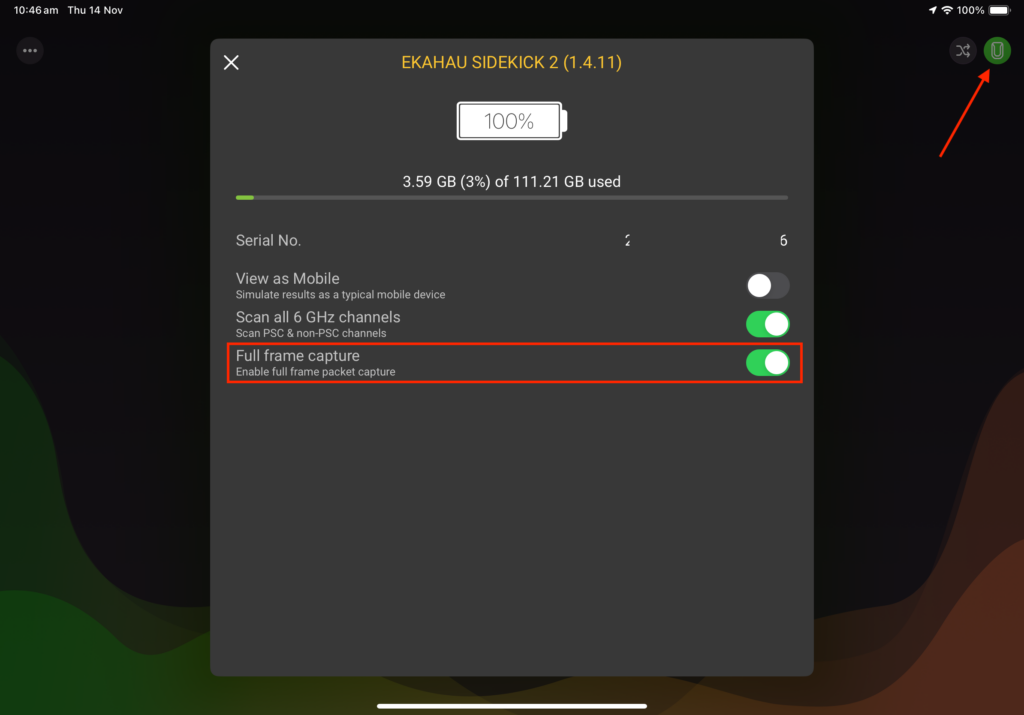
Lastly, the full 802.11 frame must be present – including both the header and the data payload. If you are capturing traffic using an Ekahau Sidekick 2, be sure to set the capture mode to “Full frame capture” in the sidekick general settings of the Analyzer app for iOS, as shown below:
Launch the packet analyzer tool from within Ekahau Analyzer and select packet Capture. Click the link to download Ekahau Analyzer for iOS. As a side note, click the link to download Ekahau Survey app for iOS.
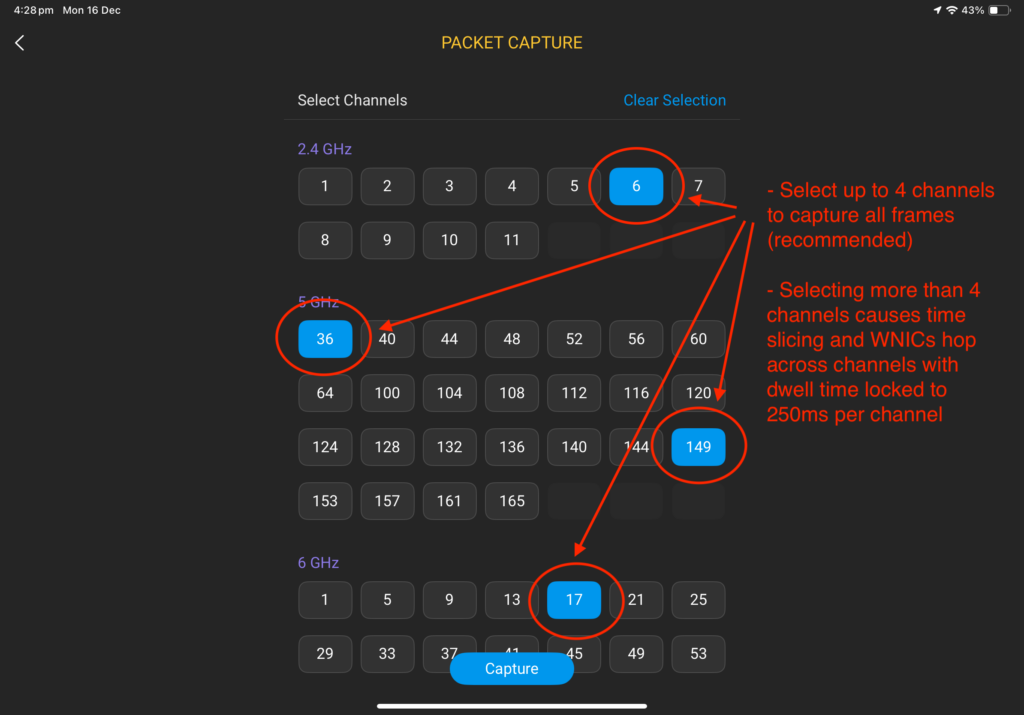
Select up to four channels to capture. Each of the four WNICs in the SK2 is assigned and locked to one of four channels selected. In the latest versions of Analyzer, it is possible to select more than four channels, however this creates a time slicing situation in which each WNIC listens on a channel for 250ms (statically set), before cycling through additional channels. As a result, your packet capture may be missing important frames for analysis, as the WNICs were not listening on that channel when the frames were transmitted.
Watch for the warm fuzzy as the capture size increases, confirming packets are being captured. Once frames of interest have been captured, click stop to end the survey.
The PCAP is copied over from the SK to iOS device. Once transferred, you can select from many options on how to transfer the file, including: iCloud, Dropbox, OneDrive, Google Drive, email, text, or even carrier pigeon… well, I’m joking about carrier pigeon, but the point is there are many methods available to transfer the PCAP from your iOS device.
Note: The Ekahau Analyzer app for iOS also supports the SK1. Be sure to use the correct cables when connecting to your iOS device (USB cable must support data pins). Additionally, packet capturing is NOT currently supported in the Android version of the Analyzer app. Finally, packet capturing with SK1 is no longer supported on Windows/macOS using the Ekahau Capture utility. At present all packet capturing must be done using the Analyzer App on iOS.
Decrypting WPA2-Enterprise/.1X Traffic
To decrypt WPA2-Enterprise/.1X traffic a few pieces of information are required and must be known.
- RADIUS key (or shared secret) must be known.
- Wireless capture of the traffic intended for decryption. The capture must include the 4-way handshake between supplicant (client) and Access Point.
- Authenticator exchanged between the Authentication Server (AP or WLC) & Authenticator (RADIUS) from the final Access-Request packet.
- MS-MPPE-Recv-Key exchanged between the Authentication Server (AP or WLC) & the Authenticator (RADIUS) found in the Access-Accept packet.
Depending on the architecture of your WLAN solutions the authenticator may be centralized using a wireless controller (WLC) or distributed with each AP acting as an authenticator. In either case, all devices acting as an authenticator should be added to the authentication server as an authentication client permitted to communicate with each other to exchange EAP authentication messages.
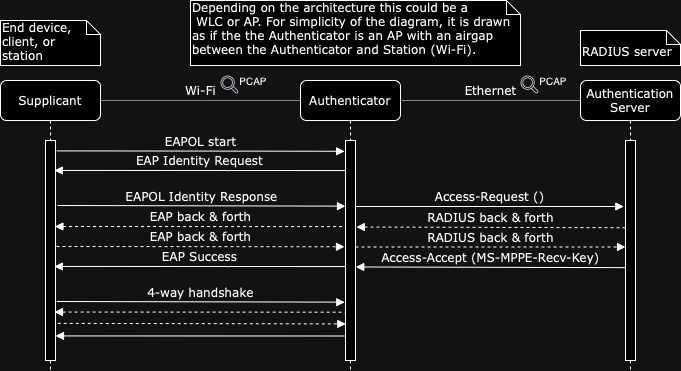
With this information in hand the following steps can be performed to decrypt traffic to and from the client.
- Extract PMK – sounds simple, but there are a few steps to collect a utility included with FreeRADIUS – “radsniff”.
- Use the extracted PMK to derive PTK. All 4 frames of the 4-way handshake must be present in the PCAP. Without these four frames, Wireshark will not be able to decrypt the traffic.
- Decrypt traffic – Wireshark automates this for us once the PMK is added to the built-in 802.11 decrypter.
Using the FreeRADIUS Utility – radsniff
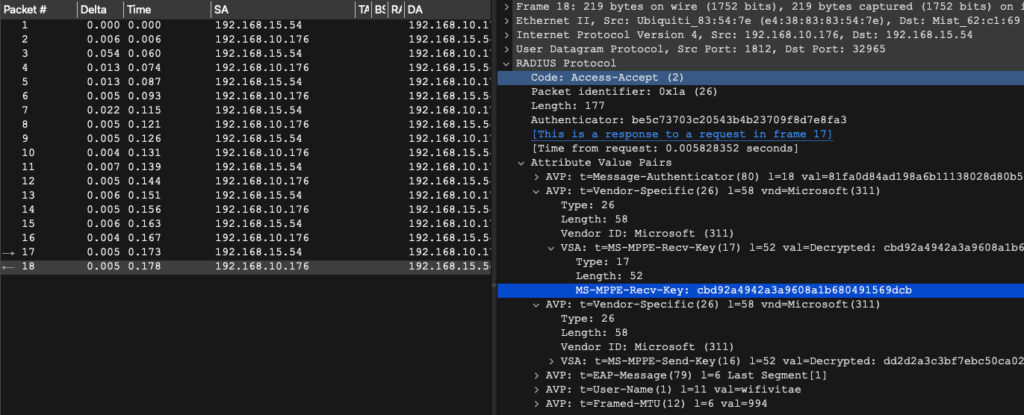
Capture initial exchange between the authenticator (WLC or AP) and authentication server (RADIUS). You are looking for the frame sent by the authentication server marked as the Access-Accept message within RADIUS Protocol. Within this frame there is a MS-MPPE-Recv-Key value. This is used by the utility to recover the MSK. In this image the is shown as cbd92a4942a3a9608a1b680491569dcb.
Once you have confirmed the required frames are in the capture, run the radsniff utility as follows and direct the output to a text file called dump.txt:
radsniff -x -I radius-authenticator.pcsp -s [RADIUS_shared_secret] > dump.txtExample output from dump.txt.
2024-10-04 10:11:02.457691 (18) Access-Accept Id 26 wired-webload-854385ab-163b-495f-aa41-c240c875c2e4.pcapng:192.168.15.54:32965 <- 192.168.10.176:1812 +0.178 +0.005
User-Name = "wifivitae"
Framed-MTU = 994
EAP-Message = 0x03e50004
Message-Authenticator = 0x81fa0d84ad198a6b11138028d80b58d0
MS-MPPE-Send-Key = 0x47a35f04b1e6117651b6ce61a38d9d5c2b37a853e17563afa3d291b1bb8d9160
MS-MPPE-Recv-Key = 0x724430df7ec4fc78e60bd581b5429ee06ef50b9b77a88dbac2115506e53a23d3
Authenticator-Field = 0xbe5c73703c20543b4b23709f8d7e8fa3
Done reading packets (wired-webload-854385ab-163b-495f-aa41-c240c875c2e4.pcapng)
Done sniffingThe value that needs to be added to Wireshark is the MS-MPPE-Recv-Key from the output above in the Access-Accept message from the Authentication Server (RADIUS) to the Authenticator (AP).
Although the value returned from radsnff is called ‘MS-MPPE-Recv-Key’, it differs from the MS-MPPE-Recv-Key shown in the PCAP above and is actually the PMK.
Add the ‘MS-MPPE-Recv-Key’ (PMK) from radsniff, minus the ‘0x’ from the beginning to Wireshark to decrypt the traffic sent over the air between the client (station) and the access point.
Decrypt Tool in Wireshark
With the PMK extracted, decryption is relatively trivial in Wireshark.
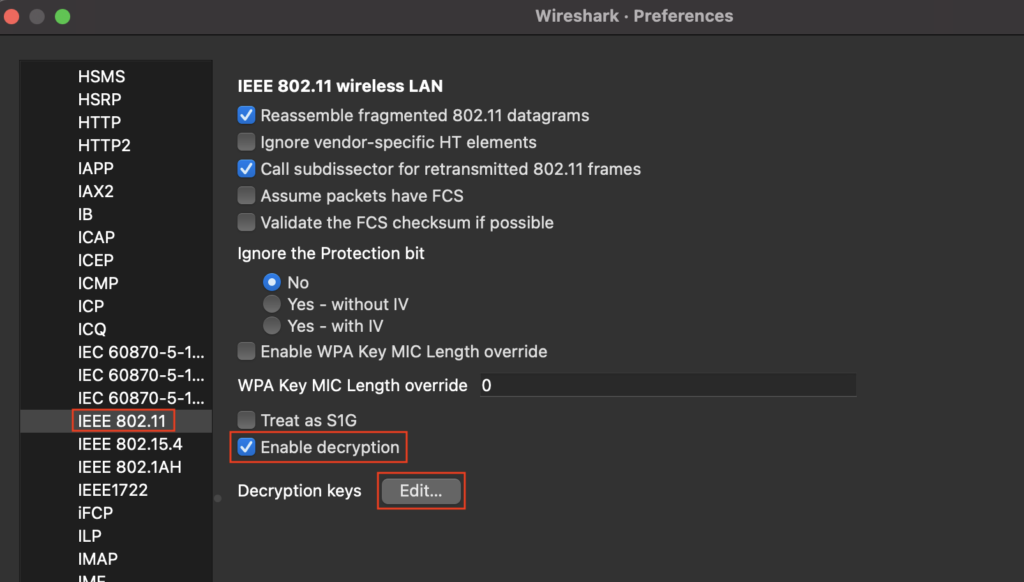
Decryption keys can be added to Wireshark’s 802.11 preferences with support for up to 64 keys.
Mac: Go to Wireshark > Preferences > Protocols > IEEE 802.11
Windows: Go to Edit > Preferences > Protocols > IEEE 802.11
Check “Enable decryption”
Click “Edit” beside Decryption key to enter the key(s)
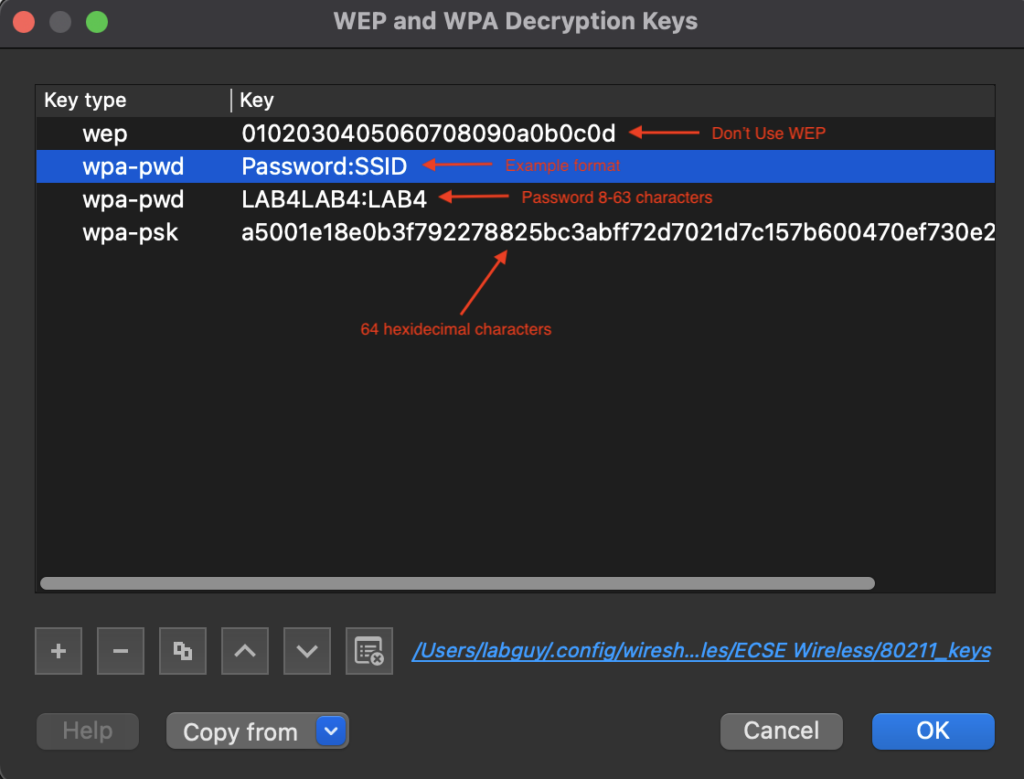
The window that pops up should look similar to below:
After clicking Edit, you should see a window similar to the one shown below:
Click on ‘+’
Choose the Key-type as wpa-psk from the dropdown.
wpa-pwd The passphrase (pwd) and SSID are used by the decrypt tool in Wireshark. This is typically the information used with PSK (Personal). It is typically entered using the following format:
passphrase:SSID
or
passphrasewpa-psk The key is parsed raw and should be 256-bits or a string of 64 hexidecimal characters. This is typically the information used with 802.1X (Enterprise), such as shown below:
PMK:SSID
or
PMKIf only the Password is provided, Wireshark will try to decrypt packets for the last-seen SSID. Your mileage may vary as the last-seen SSID may not be the SSID you are looking for.
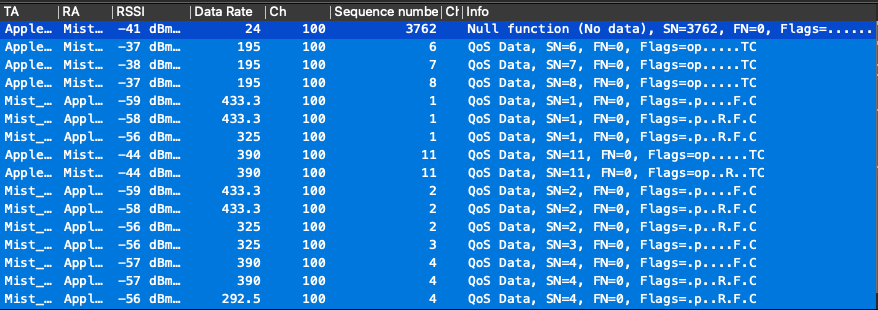
Here is an example of how the PCAP appears prior to applying the PSK in Wireshark. As the payload is still encrypted, packets are generically identified as ‘QoS Data’.
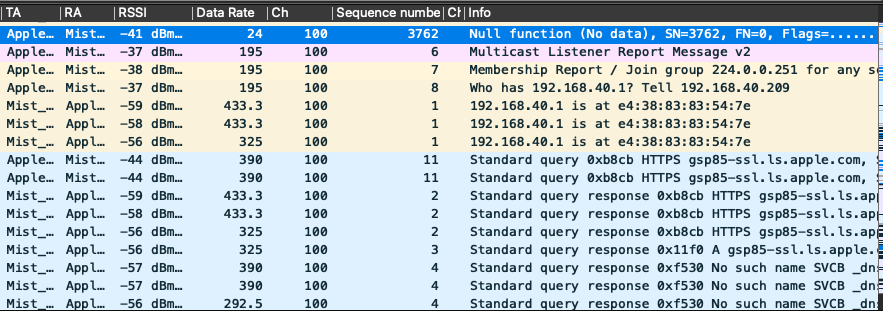
Here is an example of how the PCAP appears after applying the PSK in Wireshark. You can now see upper layer protocol information in the decoded packets.
Slàinte!
Resources
Hacking Exposed Wireless, Third Edition: Wireless Security Secrets & Solutions
(3rd Edition) by Joshua Wright (Author), Johnny Cache (Author)
WPA2 Enterprise Example
https://wiki.wireshark.org/HowToDecrypt802.11
Wireshark example
https://ask.wireshark.org/question/4050/how-to-decode-radius-ms-mppe-recv-key